Andy Grove fled from Hungary to save himself from the communists. He received an education in engineering which allowed him to lead the personal computer revolution as the CEO of the giant Intel. He died...
Andy Grove fled from Hungary to save himself from the communists. He received an education in engineering which allowed him to lead the personal computer revolution as the CEO of the giant Intel. He died in early 2018 in Silicon Valley after a long battle with Parkinson’s disease.
Perhaps it is worth taking seriously the fears of one of the most powerful people in the world who encourages us to be paranoid? Andy was not the only influential person who warned us strongly, by the way. The director of the FBI, who recently paid a million dollars to hackers to unlock an iPhone, has called on citizens to cover their webcams.
You follow the laws and so it seems you have nothing to worry about. The British government tells us: «If you have nothing to hide, then there is nothing to fear.»
However, British citizens have reasons for concern. And besides, they have good reasons to protect their devices, files, and messages with their loved ones.
"If one would give me six lines written by the hand of the most honest man, I would find something in them to have him hanged." — Cardinal Richelieu in 1641
In this article we will show you how you can protect yourself and your data using modern cryptography methods. With just a little effort you can make significant progress in protecting your own data.
Common sense security for everyone
Everything that you read in this article is absolutely free and legal. If you are worried about the reliability of the doors to your apartment, then you should also think seriously about your personal data.
«Be prepared» — The scout motto
Well, let’s start preparing.
To begin with, a few explanations. When we use the term «attacker» we mean that someone is trying to access your data without your consent. And it does not matter who it is: a hacker, a corporation, or a government.
And when we use the terms «private» or «secure» we use them reasonably. The real state of affairs is such that while people are included in the process of information exchange, there will always be a place for the human factor.
Tip #1. Use two-factor authentication on your inbox.
Your mailbox is a «skeleton key» to your life. And if an attacker compromises it, he can not only read your e-mails, but also reset all of your passwords. In general, in their hands they can have almost complete access: from social networks to bank accounts.
The simplest thing you can do to radically improve your security is to enable two-factor authentication on your inbox.
In principle, two-factor authentication is a second level of security when entering the system. Usually this involves receiving a text message with a special code when you sign in to your account. Two-factor authentication significantly reduces the likelihood of the hacking of your inbox.
Gmail users can activate two-factor authentication here.
Tip #2. Encrypt your hard drive.
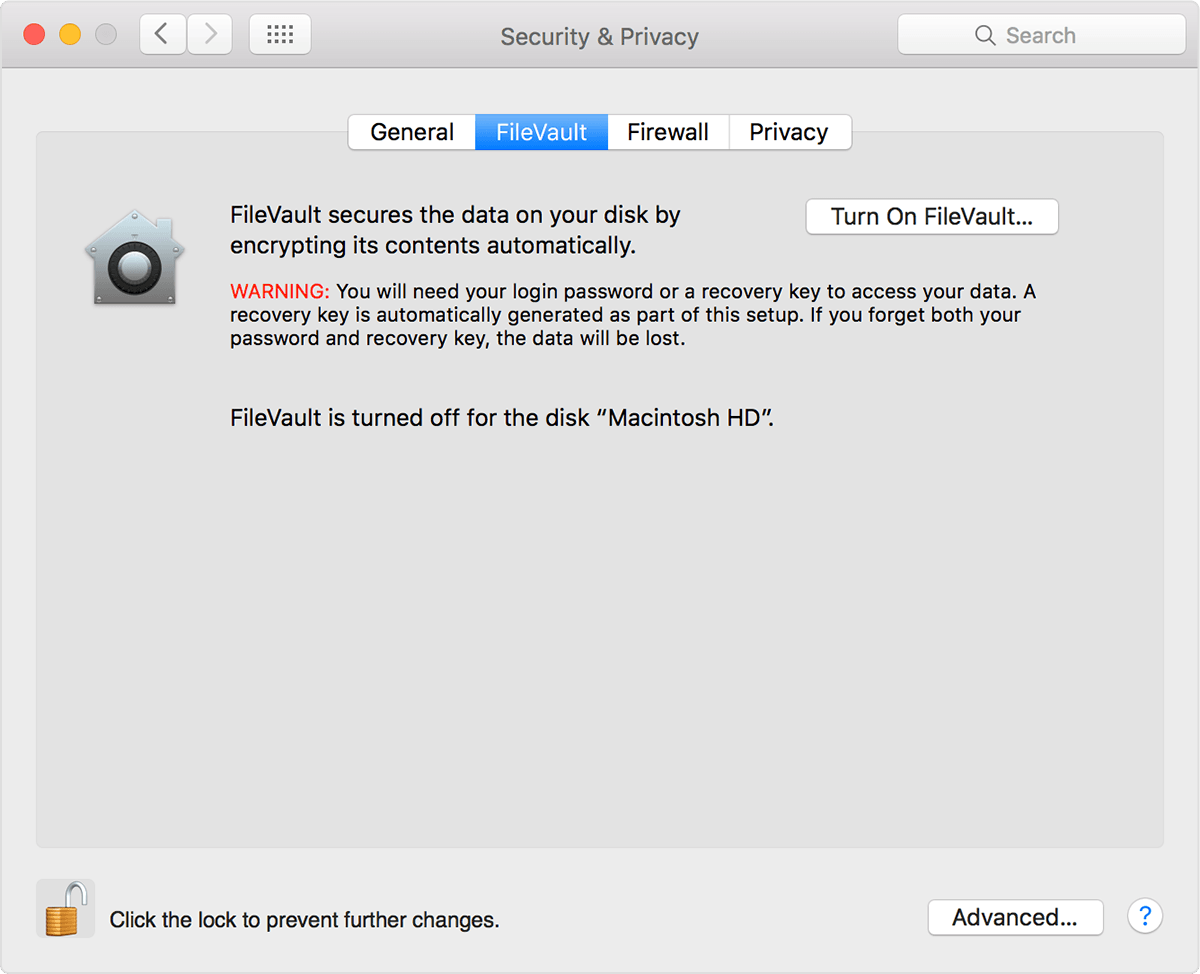
Both Windows and MacOS have a built-in ability to encrypt the hard drive. You just have to turn it on.
Tip #3. Turn on your phone’s password protection.
Authentication with a thumbprint is better than nothing, but often it is not enough.
The fifth amendment (giving the right not to testify against oneself) allows you to keep your passwords secret. However, the court reserves the right to force you to unlock the phone with a thumbprint. Also, you are unlikely to succeed in changing your thumbprint once an attacker gains access to the phone.
Typically, an attacker has 10 attempts before the phone is completely blocked. Therefore, if your four-digit password is the same as another password, or too simple, we recommend that you change it immediately.
Tip #4. Use different passwords for each service
Passwords are inherently insecure.
Mark Zuckenberg used the password «dadada» on his Linkedln account. A year ago, a list of 117 million combinations was published by hackers, his password was included in this. Knowing his email, hackers could then access his Twitter and Pinterest accounts.
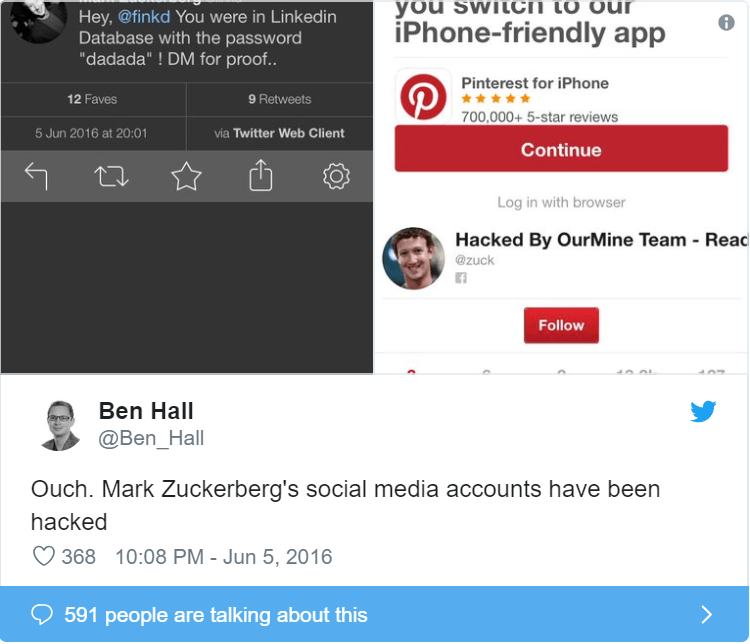
Lesson from the story: do not use the same password on different sites. Of course a ton of passwords can lead to confusion, so you can use a password manager.
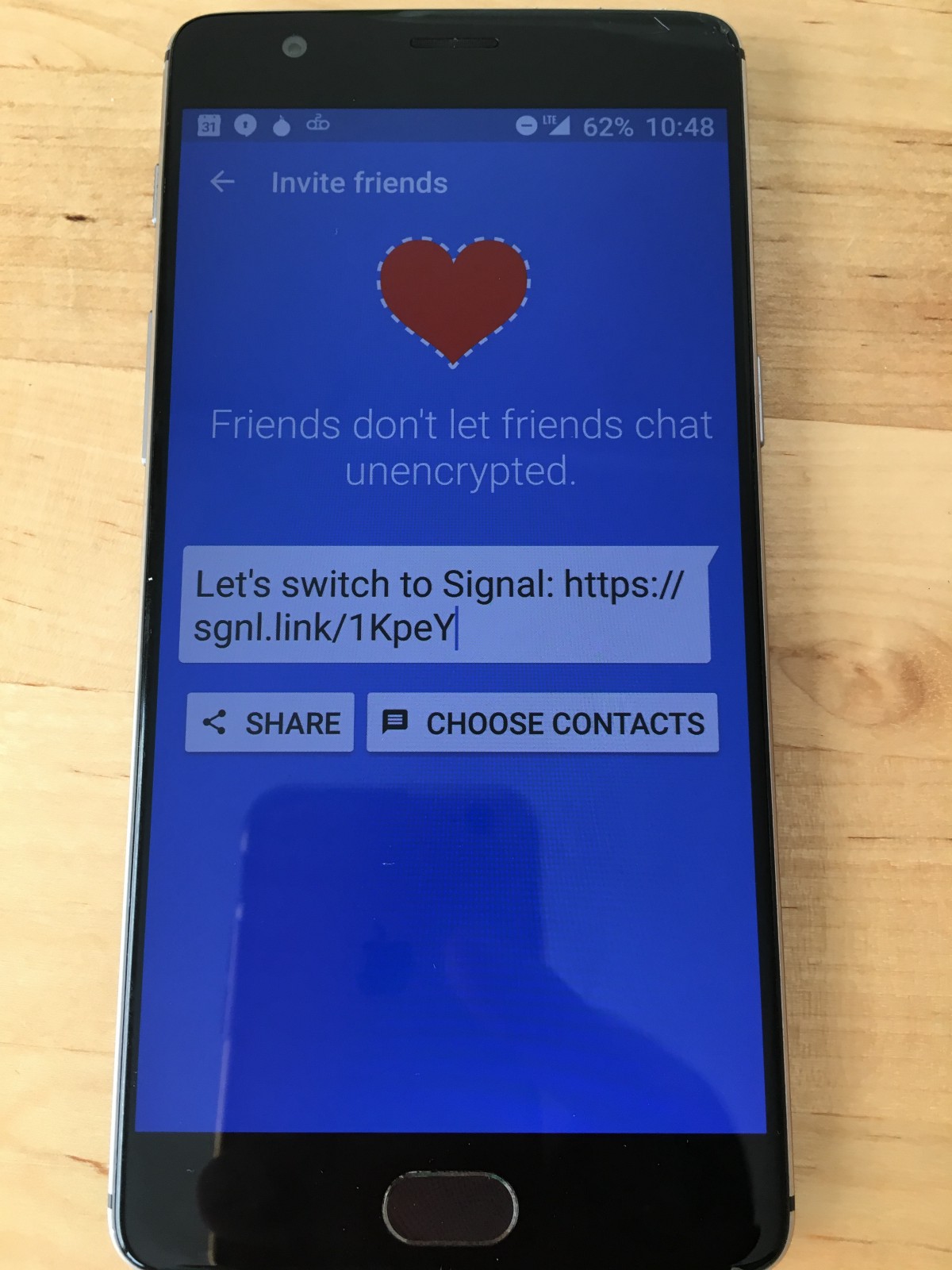
Tip #5. Send private messages using the Signal
Signal is a popular service for messaging, highly rated by Electronic Frontier Foundation. You can do everything that you usually do with text messages, for example, group messages and send photos and videos. It has all the standard messenger features: you can send messages, photos, videos, and create group chats. With one important exception: everything is encrypted.
The app can be downloaded for free on the iOS and Android app stores. The source code is publicly available.
Tip #6. Your browser’s incognito mode isn’t private enough
If you think that by using incognito mode in Chrome or private browsing in Firefox that no one will be able to track your activity, then you are mistaken. Here is who still has access to your network activity:
- Your ISP
- System administrators responsible for the network at your school, workplace, or anywhere else
- Google, Internet Explorer, Safari, Opera, and any other browser that you use.
If you want to make surfing on the Internet 100% private, use Tor.
Tip #7. Browse in private with Tor.
Tor stands for «The Onion Router». The word «onion» in the title is a reference to the multiple layers to mask network activity. Tor, just as Signal, is free to use and its source code is open access.
Step #1. Download the Orbot

Step #2. Install the Orfox browser
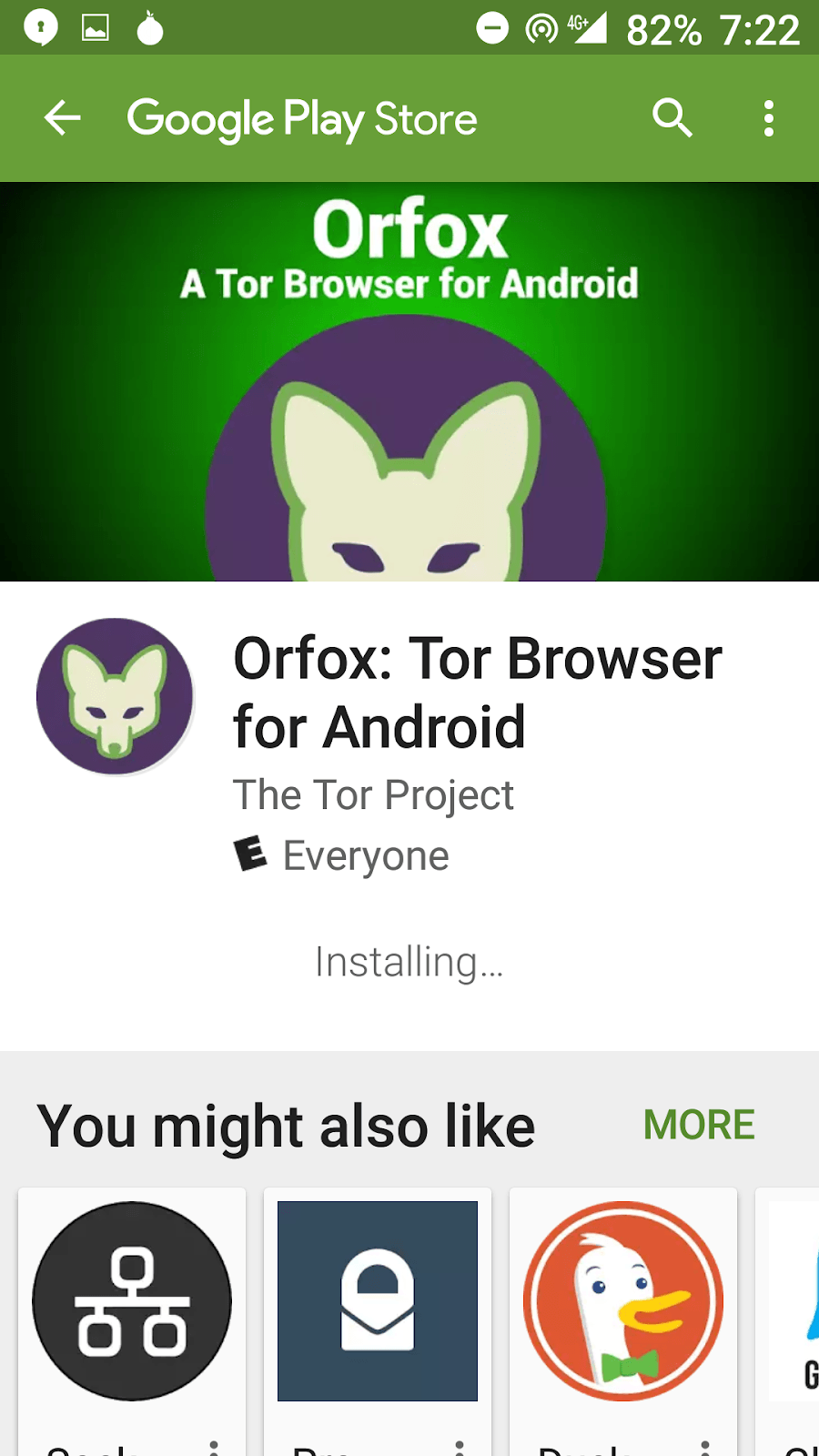
Step #3. Open Orbot
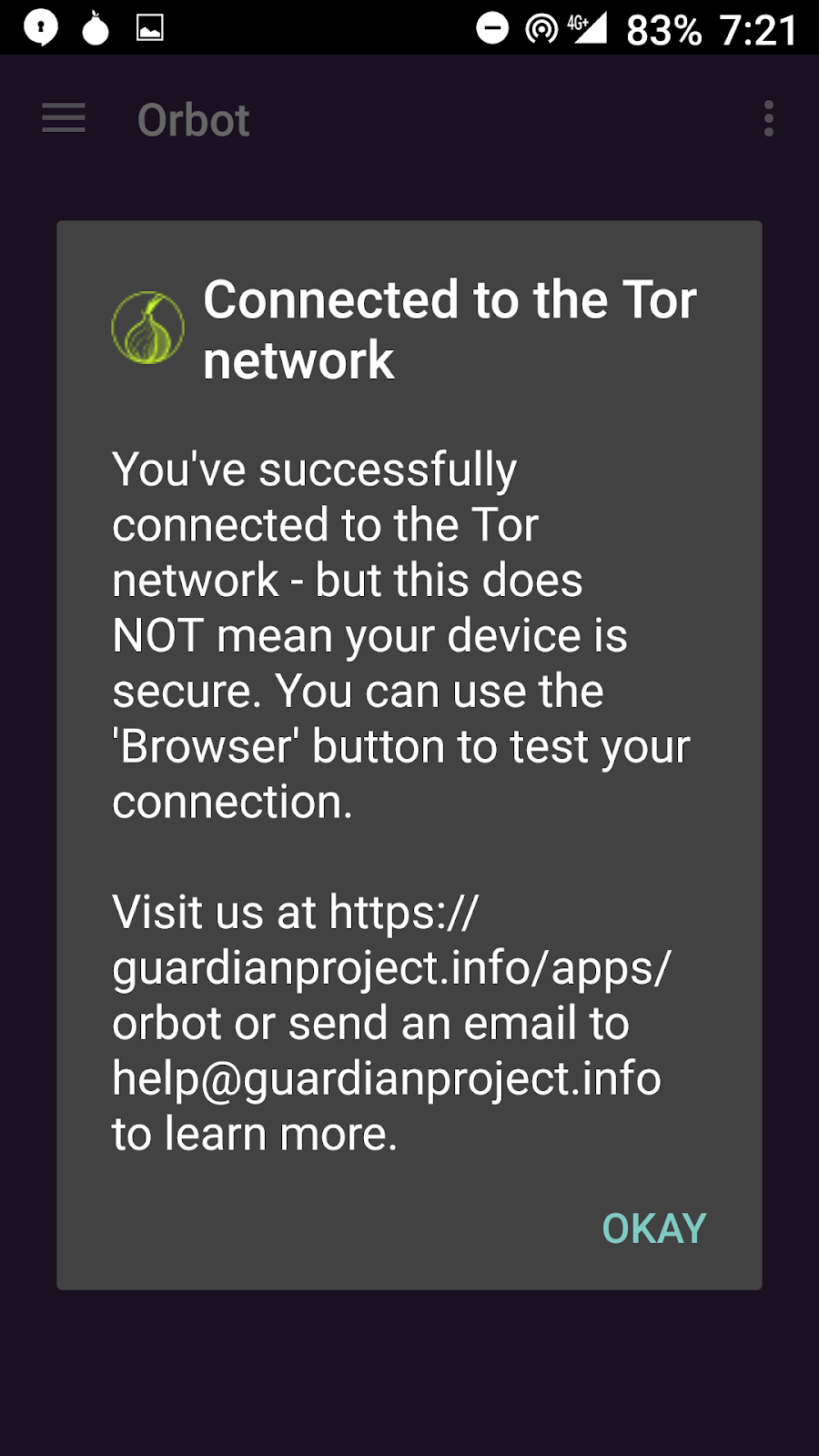
Step #4. Open Orfox
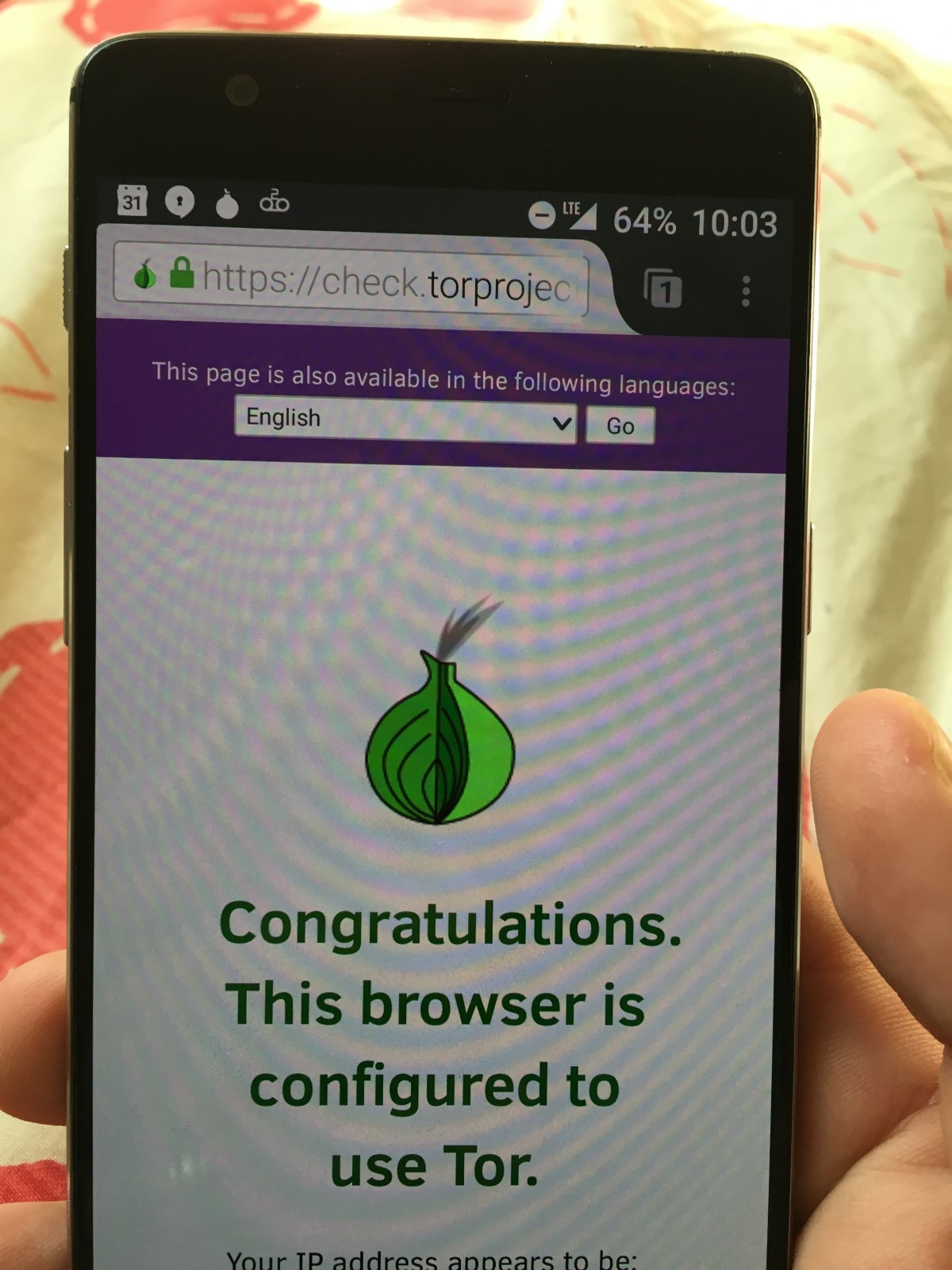
Step #5. Verify if it worked.
Visit check.torproject.org to make sure everything works. Congratulations, now it’s safer to use the internet!
Tip 8: search in private
If Tor is not convenient enough for you, you can at least use the search engine DuckDuckGo. This search engine that does not track you.
Of course, there are not as many engineers working on DuckDuck as over at Google, but the browser allows you to get Google’s encrypted search queries.

In addition, we recommend that you read the book of the computer security expert, Bruce Schneier; «The Hidden Battles to Collect Your Data and Control Your World»).
Original:
https://medium.freecodecamp.org/tor-signal-and-beyond-a-law-abiding-citizens-guide-to-privacy-1a593f2104c3
Share this with your friends!






Be the first to comment
Please log in to comment